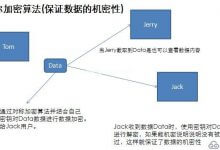
介绍如何通过加密算法实现数据的完整性、机密性及身份验证
一般互联网上加密算法分为三种: 对称加密、单向加密、非对称加密 下面就来介绍下如何通过上面的三种加密算法实现数据的机密性、完整性及身份验证。 对称机密算法: 对称加密算法提供加密算法本身并要求用户...

一般互联网上加密算法分为三种: 对称加密、单向加密、非对称加密 下面就来介绍下如何通过上面的三种加密算法实现数据的机密性、完整性及身份验证。 对称机密算法: 对称加密算法提供加密算法本身并要求用户...
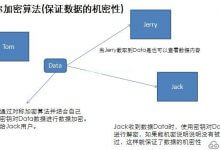
Generally, there are three encryption algorithms on the Internet: Symmetric encryption, one-way encryption, asymmetric e...

1 introduction IPtable works in OSI network layer and data link layer Exle Zan () QR code Share X Share to X Reward Pre...

Last night, I was lying in bed doing nothing to sum up and review the learning achievements since the next class on the ...

In the post epidemic era, the path of small and medium-sized enterprises' recovery is "new". In order to better serve sm...

In summary, the relationship between SUSE and HPE is complex. HPE consolidated its non core software assets with micro f...

总之,SUSE和HPE之间的关系是复杂的。 HPE将其非核心软件资产与Micro Focus合并。 而Micro Focus则拥有一家主要的Linux提供商SUSE。 现在,SUSE已经收购了Open Stack Infrastructur...

Beijing time, March 25 evening news, according to foreign media reports, although Microsoft and Google and other compani...

According to foreign media reports, Amazon AWS Cloud Service announced on Friday that it would allocate $20 million in s...

In December, Amazon, the leader in the cloud computing industry, filed a lawsuit against the Pentagon, accusing it of gi...

In December, Amazon, the leader in the cloud computing industry, filed a lawsuit against the Pentagon, accusing it of gi...

Two weeks ago, on the 10th anniversary of meituan, Wang Xing stressed to employees in an internal letter that meituan wo...